Forensic search from the Files tab
The Files tab in the Capture Engines window displays a listing of all the capture files saved to the Capture Engine. Performing a forensic search from the Files tab lets you sort through hours or even days worth of network traffic, from one or more Capture Engine capture files, for specific data you wish to analyze further.
IMPORTANT: One or more capture files saved to the Capture Engine computer are required before you can perform a forensic search.
To perform a forensic search from the Files tab:
1. From the Capture Engines window, select the Files tab of a connected Capture Engine.
TIP: Right-click inside the list of files for additional options for performing a forensic search, grouping files, uploading and downloading packets, deleting files, synchronizing files to the file system on the hard disk, and refreshing the display.
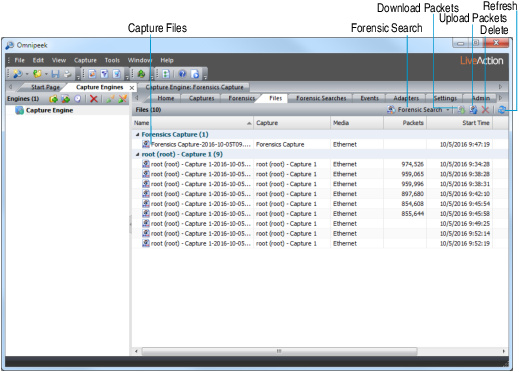
2. Select one or more capture files you wish to search.
3. Click (or click the small down arrow next to Forensic Search and select the type of forensic search you wish to perform). The Forensic Search dialog appears.
NOTE: Selecting one of the pre-defined types of forensic searches displays the Forensic Search dialog with the Analysis & Output options pre-configured for that type of forensic search. You can change any option prior to clicking .
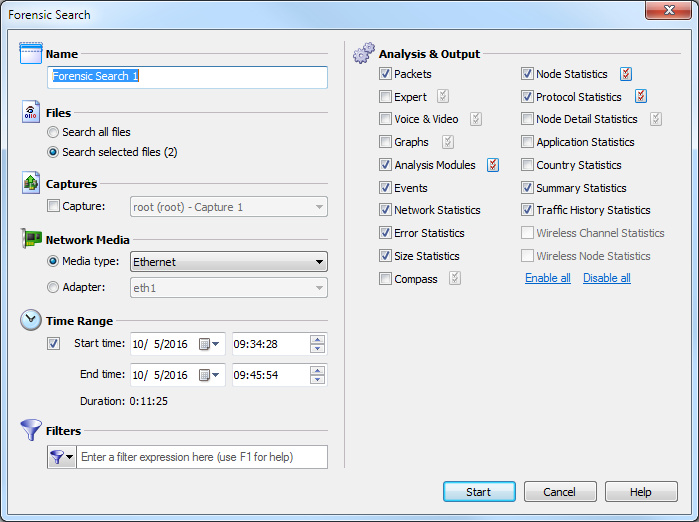
4. Complete the dialog to specify the criteria for extracting data from the selected capture files:
• Name: Enter a name for the forensic search.
• Files: Choose one of the following:
• Search all files: Select this option to search through all of the files listed in the Files tab.
• Search selected files: Select this option to search through only the selected files in the Files tab.
• Captures: Select this option and then select the capture to search from those listed in the Capture column of the Files tab.
• Network Media: Choose one of the following:
• Media type: Select this option and then select the media type to extract only the data of a specific media type.
• Adapter: Select this option and then select the adapter to extract only the data captured by a specific adapter.
• Time Range: Select this option and then configure the start and end times to extract the data.
• Start time: Set the start date and time for extracting data. Only the data captured between the start time and end time is extracted.
• End time: Set the end date and time for extracting data. Only the data captured between the start time and end time is extracted.
• Duration: Displays the amount of time between the specified start and end times.
• Filters: Click to select a filter from the display list. All packets will be accepted if no filters are applied to the forensic search.
To create an advanced filter, click Filters and select Insert filter, Insert Operator, or Insert Expression from the display.
• Analysis & Output: Select one or more of the options to enable and display that particular view in the new Forensic Search window. For various Analysis & Output options that have additional configurable settings, click the submenu to the right of the option.
5. Click . A new Forensic Search window appears along with two progress bars at the top of the window. (Clicking stops the search and then completes the processing of the packets.)
Once the processing of the packets is complete, the progress bars go away and the new Forensic Search window is populated with the data found based on the criteria you selected above.
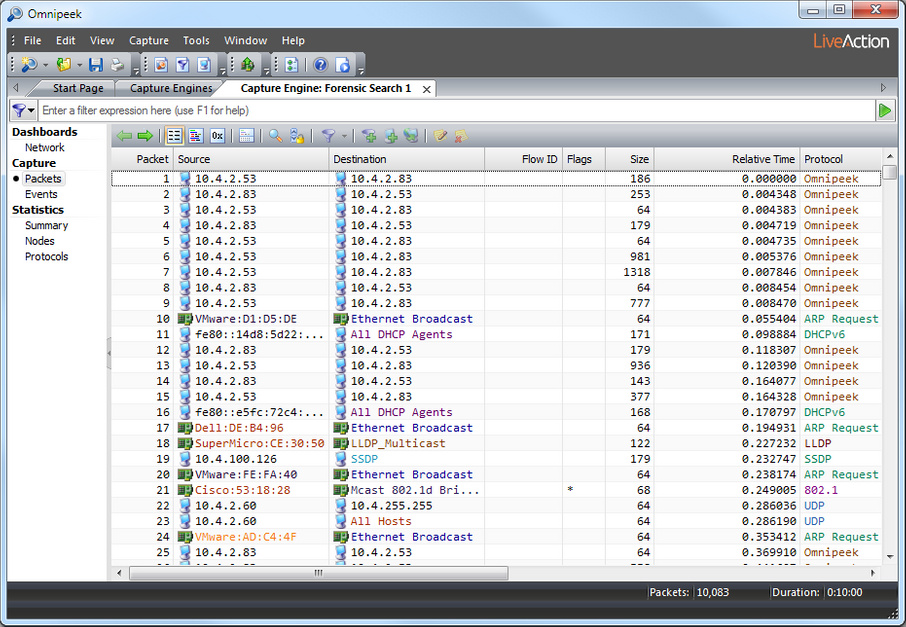
6. From the new Forensic Search window, you can further narrow down the data by performing any of the post-capture analysis methods described in the Omnipeek User Guide.